Guides
Discovering the Mystery of 127.0.0.1:49342 A Developer’s Guide to Localhost

127.0.0.1 may look like just numbers, but it plays a unique role in computer networks. It’s a loopback IP address, often referred to as “localhost.” When developers need a safe space to test code, they use localhost to keep everything within their device. Localhost is key in software development and troubleshooting, allowing testing without needing an external connection.
What is 127.0.0.1?
127.0.0.1 is an IP address that directs any network activity back to the same device. This internal network is known as a “loopback.” This address provides developers with a controlled way to interact with and test applications locally, keeping all data on the device and not sending it out to the internet. Local testing is a secure way to see how software will function in real scenarios.
Understanding Ports
Alongside IP addresses, ports act like pathways inside a device, directing data to specific applications. Ports have assigned numbers, each linking to a unique software function. Using different port numbers, developers keep their tests organized, enabling multiple software functions to run simultaneously without interference. This helps them examine each feature independently, making the development process smoother.

Purpose of Localhost
Localhost enables internal communication within the same device. For developers, it’s invaluable for testing. It isolates applications from outside networks, creating a safe, sandboxed environment. With localhost, they can experiment with software, identify issues, and make adjustments without risk to actual users or external systems. This secure setup ensures any potential problems stay contained.
Also Read: www.politicser.com Pepperboy News A New Era of Political Reporting
Basics of IP Addresses
IP addresses are like digital identifiers that allow devices to recognize each other. They come in two main forms: IPv4 and IPv6. IPv4 addresses use four sets of numbers separated by dots, like “192.168.1.1.” IPv6 addresses, meanwhile, are much longer and incorporate both numbers and letters. The extended structure of IPv6 allows for more unique combinations, supporting the rapidly increasing number of devices connected to networks worldwide.
Why Use 127.0.0.1?
127.0.0.1 is a reserved address specifically for localhost, referring to the device in use. This address makes internal communication possible, allowing developers to run tests within the device. Using 127.0.0.1, developers can check that their applications run smoothly in a controlled space, separate from the external network. This self-contained setting is ideal for spotting bugs and testing software reliability without impacting live networks.
Understanding Ports – Why 49342?
Ports work with IP addresses to send data within a device, like channels connecting different applications. When developers choose a port like 49342, they set a specific path for certain tasks. Each port number corresponds to a unique program or function, allowing a single device to handle multiple connections efficiently. By assigning distinct ports, developers keep everything running smoothly and can troubleshoot issues more easily.
Also Read: Mysk2 Dyndns Org 3: How to Set Up Your Dynamic DNS?
Purpose of Specific Ports

Developers can manage and test separate software components by assigning unique ports, such as 49342. This targeted approach enables them to run different functions simultaneously without conflicts. Each port, being dedicated to a specific purpose, allows developers to examine each part of their application in isolation. Specific ports also make it simpler to detect and resolve errors.
How Developers Use Localhost and Port 49342
Testing with 127.0.0.1:49342 gives developers a safe way to work with their software. They can run tests directly on their machine without risking any external connections. Local testing lets developers examine how applications interact under real conditions, spotting any potential issues in a controlled setup. By isolating these tests on localhost, they can refine the code and address errors without any risks to users or networks outside.
Also Read: Gimkit Host: How to Create a Successful GimkitHost?
Debugging Programs
Using localhost at port 49342 helps developers troubleshoot and debug their applications. Running tests in this environment allows them to pinpoint problems within the code, find bugs, and fix them before deploying software to a live setting. Debugging locally reduces the likelihood of emerging issues in production environments, ensuring smoother operation once the application is accessible to users.
Network and Security Basics with Localhost
Localhost is a secure network setup because it does not expose the device to outside connections. When using 127.0.0.1, data flow stays contained within the same device, making it ideal for safe testing. Developers can work on their software without the risks of open network exposure. Localhost setups are safe by design, and by managing which ports are active, such as 49342, developers can prevent any accidental external access.
Managing Port Security

Ports play a role in device security. Developers monitor which ports are open or active, especially when testing on localhost. Ensuring only necessary ports, such as 49342, are accessible helps avoid vulnerabilities. Managing port access effectively keeps the testing environment secure, limiting potential exposure to outside networks or unintended connections.
Also Read: 127.0.0.1:62893 for Beginners: An Introduction to Localhost and Error Fixes
Advanced Applications of Localhost in Development
Developers often need multiple ports for complex applications to handle different system parts. Each port can manage a separate task, like handling user requests on one port and processing data on another. This arrangement keeps everything organized and allows for easier troubleshooting. In virtual environments, localhost settings and port assignments are essential for managing interactions within virtual machines or containers. Platforms like Docker use this setup to isolate tasks, ensuring each part works seamlessly without conflicts.
Using Multiple Ports
In advanced setups, multiple ports may be necessary to manage various tasks. Each port handles a distinct function, keeping each application part separate and organized. This separation of duties simplifies debugging and allows developers to address issues quickly. By using designated ports, developers gain better control and can test each part of the application independently.
Real-Life Uses of 127.0.0.1:49342
Application servers like Apache or Nginx use localhost and distinct ports to manage network requests securely. Each port enables different services, helping data move smoothly and securely. In cloud development, localhost addresses and ports like 49342 allow developers to test and refine their applications before making them accessible to a live audience. Cloud platforms allow developers to manage network configurations, ensuring testing environments function without disrupting other systems.
Also Read: Money6x.Com Earning – Everything You Need to Know
Conclusion
Understanding localhost and ports, especially using 127.0.0.1:49342, is essential for safe and efficient development. Local testing allows developers to refine and troubleshoot their software without the risks associated with live environments. By controlling IP addresses and ports, developers can better organize their applications and manage security. Knowing these network fundamentals helps create stable, reliable applications, making development processes smoother and more secure.
Guides
How to Install FreeDoor 2.4.6.8: A Complete Step-by-Step Guide

FreeDoor 2.4.6.8 is a lightweight anti-censorship tool developed by Dynamic Internet Technology (DIT), primarily designed to help users access blocked websites in regions with heavy internet restrictions. It operates using a proxy mechanism similar to FreeGate, offering a simple and portable alternative to full-scale VPN services.
Though it’s not as widely used today, FreeDoor still holds value for those seeking a fast, minimal, and easy-to-use proxy solution.
What is FreeDoor 2.4.6.8?

FreeDoor is part of a suite of tools developed by DIT to promote internet freedom. Version 2.4.6.8 is one of its most stable releases, providing users with a means to bypass censorship without requiring extensive configuration. Unlike VPNs or browser plugins, FreeDoor runs as a standalone executable and doesn’t require installation or administrative access on Windows machines.
How to Fix Left 4 Dead 2 Install Problems, Freezes and Errors
Step-by-Step Installation Guide
Step 1: Download FreeDoor 2.4.6.8
Begin by finding a reputable source for downloading the tool. Since FreeDoor is no longer officially maintained, you’ll need to rely on trusted third-party archives or mirror sites. Be cautious and scan any files for malware before use.
Search for “FreeDoor 2.4.6.8 download” and verify the file name — it should be something like fd.exe or freedoor2468.zip.
Step 2: Extract the ZIP File
Once you’ve downloaded the ZIP file, right-click it and select “Extract All” or use tools like WinRAR or 7-Zip. Choose a destination folder that’s easy to access, such as your Desktop or Downloads directory.
Step 3: Launch FreeDoor
Inside the extracted folder, you’ll find the main executable file (usually named fd.exe). Double-click the file to run FreeDoor. Since it’s portable, it will launch directly without installing anything on your system.
You might see a Windows security prompt — click “Run Anyway” if you trust the source. If your antivirus flags it, temporarily disable the antivirus, or whitelist the app — but only if you’re confident the file is clean.
Step 4: Wait for Connection
When FreeDoor launches, it attempts to establish a connection through DynaWeb proxy servers. This may take a few moments depending on your network.
Once connected, the interface will notify you that it’s ready. You’ll also see your browser open to a test page or homepage confirming the tool is working.
Step 5: Browse the Web
After connection is established, FreeDoor will automatically configure your Internet Explorer or default system browser to use its proxy. You can now browse previously inaccessible websites. If you’re using another browser (like Chrome or Firefox), you may need to manually set the proxy to match FreeDoor’s settings (usually 127.0.0.1 with a specific port like 8580).
How to Fix GTA IV Crashes and Freezings on PC?
Troubleshooting Tips
If FreeDoor fails to connect:
- Check your firewall or antivirus settings.
- Try a different Wi-Fi network or restart your router.
- Use the built-in “Retry” option or close and reopen the app.
If performance is slow, keep in mind that proxy-based tools like FreeDoor are more lightweight but often less stable or fast than VPNs.
Is FreeDoor Still Safe to Use?
FreeDoor 2.4.6.8 is considered outdated by modern standards, but it can still be effective in certain environments. However, since it’s no longer actively developed or officially supported, security vulnerabilities are a possibility. Always download from a known safe site, and consider running it in a virtual machine or sandbox for added protection.
Final Thoughts
FreeDoor 2.4.6.8 remains a useful tool for bypassing online censorship in a quick and portable way. While not as robust as a VPN, it provides a no-frills solution that many still find helpful, especially in regions with restricted access to the open internet. Use it responsibly, stay safe, and always keep your digital privacy in mind.
Guides
How to Find IP Addresses in Online Games: Methods, Risks, and Considerations
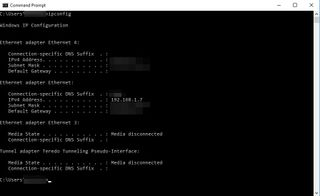
In the world of online gaming, understanding network connections can be important for troubleshooting issues, optimizing performance, or protecting yourself from potential security threats. This article explores the legitimate methods to identify IP addresses in gaming environments, while emphasizing the ethical considerations and potential risks involved.
Understanding IP Addresses in Gaming
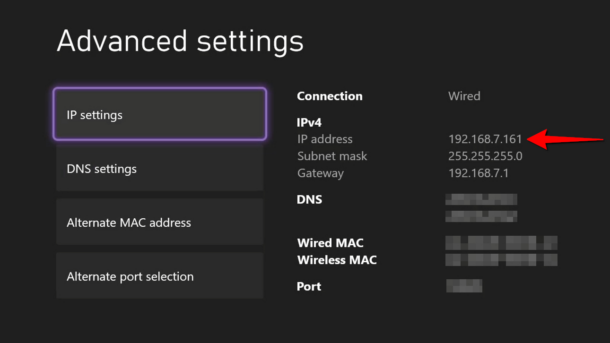
An IP (Internet Protocol) address is a numerical label assigned to each device connected to a computer network. In gaming, IP addresses serve as digital identifiers that allow data to be exchanged between your device and game servers or other players.
Legitimate Reasons to Find IP Addresses
Before exploring methods, it’s important to understand when identifying IP addresses might be appropriate:
- Troubleshooting connection issues
- Setting up dedicated servers or LAN parties
- Diagnosing network performance problems
- Securing your own network from suspicious activity
- Also Read – Fun Guaranteed Games You Can Play Online
Common Methods to Find IP Addresses in Games
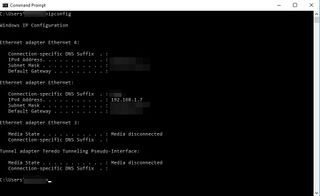
1. Using Built-in Game Features
Many games provide network information through their settings or console menus:
Server browser interfaces: Games with dedicated servers often display the server IP addresses
- Network statistics screens: Found in multiplayer games under settings or pause menus
- Console commands: Some PC games allow network information display through developer consoles
2. Network Monitoring Tools
These software solutions can help identify connections your computer is making:
- Resource Monitor (Windows): Can be accessed through Task Manager → Performance tab → Resource Monitor → Network tab
- Network Utility (Mac): Provides information about active connections
- Wireshark: A more advanced network protocol analyzer that can capture and analyze network traffic
- NetStat Commands: Using command prompt/terminal to view active connections
3. Router Access
Most modern routers provide information about connected devices:
- Access your router’s admin panel (typically through 192.168.1.1 or similar)
- Look for connected devices or network statistics
- Some routers provide logs of incoming/outgoing connections
Also Read – Best Big Fish Games to Play in September
Legal and Ethical Considerations
It’s crucial to understand the legal and ethical implications:
- Only monitor your own network traffic or networks you have permission to analyze
- Respect privacy laws which vary by country and region
- Never use IP information for harassment, attacks, or other malicious purposes
- Be aware that attempting to obtain others’ IP addresses without consent may violate terms of service for many games and could result in bans
Protecting Your Own IP Address
If you’re concerned about your own privacy:
- Consider using a VPN (Virtual Private Network) while gaming
- Avoid joining suspicious servers or clicking unknown links
- Be cautious with third-party voice chat programs that may expose your IP
- Use platform features that hide network information when available
Risks of IP Address Exposure
Understanding the risks helps emphasize why ethical use is important:
- DDoS Attacks: Malicious actors might use an IP address to flood a connection with traffic
- Approximate Geolocation: IP addresses can sometimes reveal approximate geographic location
- Potential for harassment: In competitive gaming, some players might use IP information inappropriately
Conclusion
While there are legitimate reasons to understand IP addresses in gaming environments, this knowledge comes with responsibility. Always prioritize network security, respect privacy, and use these methods only for appropriate purposes such as troubleshooting or improving your gaming experience.
Remember that many games are designed to obscure direct peer-to-peer connections specifically to protect players’ privacy and security. If you’re experiencing issues, official support channels are often the best first resource rather than attempting to gather network information yourself.
Guides
Solitaire Grand Harvest Free Coins (2025)
Key points:
- Players can claim free coin links every day to keep playing without running out of resources.
- Completing missions, spinning the bonus wheel, watching ads, and joining events help earn more coins.
- Saving coins, planning moves, and stacking rewards can speed up progress in the game.
Introduction
Want to keep playing Solitaire Grand Harvest without running out of coins? You’re in luck! Free coins can help you precise levels, expand your farm, and unlock exciting rewards. With fresh coin links available daily, you’ll never have to pause your game. Whether you’re a new player or a seasoned pro, these rewards will keep the fun going. Don’t miss out—grab your free coins today and keep growing your farm effortlessly!
Solitaire Grand Harvest Free Coins Links (March 2025)
Kickstart your day with extra coins to improve your gameplay. Below are the free coin links for March 2025:
| Date | Coins | Daily Link |
| 14th March 2025 | 2,000 Coins | Collect |
| 14th March 2025 | 2,000 Coins | Collect |
| 14th March 2025 | 2,000 Coins | Collect |
| 13th March 2025 | 2,000 Coins | Collect |
| 12th March 2025 | 2,000 Coins | Collect |
| 12th March 2025 | 2,000 Coins | Collect |
| 11th March 2025 | 2,000 Coins | Collect |
| 11th March 2025 | 2,000 Coins | Collect |
| 10th March 2025 | 2,000 Coins | Collect |
| 10th March 2025 | 2,000 Coins | Collect |
| 10th March 2025 | 2,000 Coins | Collect |
| 8th March 2025 | 2,000 Coins | Collect |
| 6th March 2025 | 2,000 Coins | Collect |
| 6th March 2025 | 2,000 Coins | Collect |
| 5th March 2025 | 2,000 Coins | Collect |
| 5th March 2025 | 2,000 Coins | Collect |
| 4th March 2025 | 2,000 Coins | Collect |
| 4th March 2025 | 2,000 Coins | Collect |
These rewards are available for a limited time, so claim them as soon as possible. Check back daily to ensure you don’t miss out!
Also Read: Best and Safe ROM Sites to Download ROMs
What Is Solitaire Grand Harvest?
Solitaire Grand Harvest is a fascinating game that blends the classic solitaire experience with the excitement of farming. You can develop and improve your virtual farm by earning coins and rewards as you progress through the various stages. The game keeps things interesting with new challenges, power-ups, and bonuses, making every level more engaging than the last.
But you need coins to advance in the game; running out can make you move more slowly. Free currency links are, therefore, crucial! They let you get more rewards without paying real money, so you can keep playing, open up new areas, and quickly expand your farm.
How to Redeem Free Coins in Solitaire Grand Harvest

Redeeming your free coins in Solitaire Grand Harvest is simple. Follow these steps to claim your rewards:
- 1. Click on any of the free coin links listed above.
- 2. The link will open the Solitaire Grand Harvest app.
- 3. If prompted, log in to your account.
- 4. Once the game loads, your coins will be automatically added.
- 5. Enjoy your free rewards, and continue playing!
If a link doesn’t work, don’t worry! Some links have expiration dates or may be region-specific. Check back regularly for new working links.
Also Read: How Long Does it Take to Download Fortnite on PC
More Ways to Earn Free Coins in Solitaire Grand Harvest
In Solitaire Grand Harvest, numerous methods exist to increase your coin total besides claiming daily free coin links. Using these strategies allows you to advance more quickly and play the game uninterrupted.
1. Complete Daily Missions
You can earn free coins by completing the daily tasks Solitaire Grand Harvest offers. These missions may involve achieving set goals or clearing particular levels.
You can ensure you never miss out on extra coins by checking the daily missions tab. Your in-game balance will increase if you regularly finish them.
2. Play More Levels
Naturally, you get more coins as you progress through the game’s levels. You advance by earning specific coins for each level you finish.
The benefits get better as you advance in level. To optimize your coin profits and unlock new bonuses, it is crucial to continue playing regularly.
3. Spin the Bonus Wheel
The game has a daily spin wheel with exclusive rewards, power-ups, and free coins. This is an easy and enjoyable technique to gain extra advantages.
To improve your gaming and earn more coins without using real money, make it a habit to spin the wheel daily.
4. Invite Friends
Connecting Solitaire Grand Harvest to social media allows you to invite friends. You receive free coins for each new friend you refer who joins.
You can earn more incentives the more people you invite. While playing together, it’s a terrific way to increase your coin balance.
5. Watch Ads
Watching the short ads is one quick and easy method to get free coins in the game. Tap on the ad offers when they appear.
These advertisements often only last a few seconds but offer considerable rewards. You can swiftly grow your coin stash by watching several advertisements each day.
6. Participate in Events
Special in-game events sometimes offer massive incentives, such as free coins, power-ups, and other perks. These events have a time limit and are subject to frequent changes.
You can maximize your profits by watching upcoming events. Actively participating in them offers you a significant edge in earning extra coins.
7. Join a Community
Extra reward links and helpful advice can be found in online gaming communities like Reddit, Discord channels, and Facebook groups.
Gamers frequently distribute the most recent links to free coins and game tips. Participating in these communities keeps you informed about new coin-earning opportunities.
8. Use Power-Ups Wisely
Power-ups make it easier to finish challenging stages quickly, saving you money. Strategic use of them reduces wasteful spending.
Save power-ups for more complex levels when they can have a more significant effect rather than using them immediately. Wise use ensures better coin management.
By following these strategies and daily free coin links, you’ll never run out of coins and can enjoy Solitaire Grand Harvest without interruptions!
Also Read: How Many GB is Valorant: Storage Guide
Understanding the Farming Aspect of Solitaire Grand Harvest

Solitaire Grand Harvest incorporates an entertaining farming element compared to standard solitaire games. Besides clearing cards, you can cultivate crops, clear fields, and build your virtual farm while playing. You can acquire more land, grow more crops, and create a thriving farm with the benefits you receive for finishing each level.
Making the most money on your farm requires careful management. Bonuses increase with the quality of your expansions and upgrades. You can earn more coins by completing farming tasks, earning daily incentives, and advancing through levels. The game is kept interesting by this unique fusion of farming and solitaire!
How Many Levels Does Solitaire Grand Harvest Have?
As of November 2024, Solitaire Grand Harvest boasts over 10,000 levels, with more added regularly. Each level presents fresh challenges, keeping the game exciting and engaging. Developers frequently introduce new updates, ensuring players always have new obstacles to tackle, rewards to earn, and features to explore.
As you proceed, new farm regions, power-ups, and special bonuses that speed up your progress are unlocked. As the difficulty increases, strategy and resource management become increasingly important. Claim daily rewards, use free coin connections, and use clever gameplay strategies to maximize your earnings and improve your experience if you want to keep going smoothly!
Also Read: How Big is Fortnite? System Requirements [Complete Size Guide]
Tips to Progress Faster in Solitaire Grand Harvest

Want to level up quickly and make the most of your coins? Follow these innovative strategies to advance faster and earn more significant rewards.
1. Save Your Coins
Avoid spending coins on unnecessary moves. Use them wisely to ensure you have enough for more challenging levels.
2. Plan Your Moves
Solitaire is all about strategy. Take your time to analyze each move instead of rushing through the game.
3. Participate in Seasonal Events
Limited-time events offer rare rewards and bonuses. Joining these events can help you earn extra coins and power-ups.
4. Stack Rewards
Combine free coins, daily spins, and event bonuses. Using multiple rewards together will maximize your progress and earnings.
Also Read: PES 23 PPSSPP: Download PES 2023 PPSSPP ISO for Android
Conclusion
Solitaire Grand Harvest combines the thrill of solitaire with the joy of farming, but running out of coins can bring your progress to a halt. Luckily, there are plenty of ways to keep your balance full and your game running smoothly.
By grabbing free coin links daily and using innovative strategies, you can keep unlocking new levels, expanding your farm, and enjoying exciting rewards. The more you play, the more opportunities you’ll have to earn extra bonuses.
Don’t let a low coin balance slow you down—claim your free coins today and keep the fun going! Happy harvesting!
-

 Guides5 years ago
Guides5 years ago6 Proven Ways to Get more Instagram Likes on your Business Account
-

 Mainstream10 years ago
Mainstream10 years agoBioWare: Mass Effect 4 to Benefit From Dropping Last-Gen, Will Not Share Template With Dragon Age: Inquisition
-

 Mainstream6 years ago
Mainstream6 years agoHow to Buy Property & Safe Houses in GTA 5 (Grand Theft Auto 5)
-

 Casual1 year ago
Casual1 year ago8 Ways to Fix Over-Extrusion and Under-Extrusion in 3D Printing
-

 Mainstream12 years ago
Mainstream12 years agoGuild Wars 2: The eSports Dream and the sPvP Tragedy
-

 Uncategorized4 years ago
Uncategorized4 years agoTips To Compose a Technical Essay
-

 Indie12 years ago
Indie12 years agoCo-op Horror: An Interview With The Developers of Damned
-

 Guides1 year ago
Guides1 year agoExplore 15 Most Popular Poki Games
